If you use VLC media player on your computer and haven’t updated it recently, don’t you even dare to play any untrusted, randomly downloaded video file on it.
Doing so could allow hackers to remotely take full control over your computer system called VLC media player hacking.
That’s because VLC media player software versions prior to 3.0.7 contain two high-risk security vulnerabilities, besides many other medium- and low-severity security flaws, that could potentially lead to arbitrary code execution attacks.
With more than 3 billion downloads, VLC is a hugely popular open-source media player software that is currently being used by hundreds of millions of users worldwide on all major platforms, including Windows, macOS, Linux, as well as Android and iOS mobile platforms.
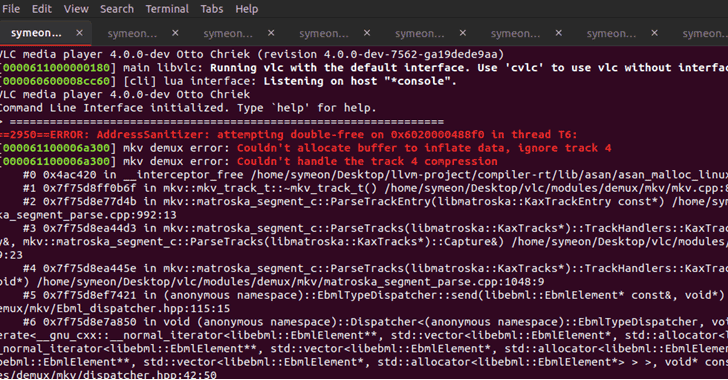
Discovered by Symeon Paraschoudis from Pen Test Partners and identified as CVE-2019-12874, the first high-severity vulnerability is a double-free issue which resides in “zlib_decompress_extra” function of VideoLAN VLC player and gets triggered when it parses a malformed MKV file type within the Matroska demuxer.
The second high-risk flaw, identified as CVE-2019-5439 and discovered by another researcher, is a read-buffer overflow issue that resides in “ReadFrame” function and can be triggered using a malformed AVI video file.
Title: Unveiling the Truth Behind VLC Media Hacking: Separating Fact from Fiction
In the vast digital landscape, where technology evolves at an unprecedented pace, rumors and misconceptions often swirl around popular software. VLC Media Player, a beloved open-source media player renowned for its versatility and robustness, is no exception. Amidst the vast sea of misinformation, the term “VLC Media hacking” has garnered attention, raising concerns and questions about the security of this widely-used software.
Let’s delve deeper into the topic to unravel the truth behind VLC Media hacking and separate fact from fiction.
Fact: VLC Vulnerabilities Exist
Like any software, VLC Media Player isn’t immune to vulnerabilities. Over the years, security researchers have uncovered and reported various vulnerabilities in VLC, ranging from buffer overflows to remote code execution exploits. These vulnerabilities, if left unpatched, could potentially be exploited by malicious actors to compromise users’ systems.
Fiction: Hacking VLC Is Common Practice
Contrary to popular belief, hacking into VLC Media Player itself isn’t a common practice. The dedicated team of developers behind VLC works tirelessly to address security vulnerabilities and release patches and updates to ensure the software’s integrity and security. While vulnerabilities may exist, exploiting them on a large scale to compromise VLC users’ systems isn’t a prevalent occurrence.
Fact: VLC Can Be Used as a Vector for Malicious Content
While hacking into VLC itself may be uncommon, malicious actors may exploit vulnerabilities in media files or utilize social engineering tactics to distribute malware through VLC. For example, attackers may disguise malware as legitimate media files and lure users into downloading and opening them with VLC. Once opened, these malicious files can exploit vulnerabilities in VLC or other software to compromise users’ systems.
Fiction: VLC Is Inherently Insecure
Despite occasional vulnerabilities, VLC Media Player isn’t inherently insecure. In fact, VLC is lauded for its commitment to security and privacy, with features like built-in codecs, support for various media formats, and robust encryption options. The VLC development team actively monitors security threats and releases updates promptly to address any vulnerabilities, ensuring users can enjoy a secure and reliable media playback experience.
Best Practices for Secure VLC Usage
-
Keep VLC Updated to prevent VLC media player hacking: To mitigate security risks, it’s crucial to keep VLC Media Player updated to the latest version. Updates often include security patches and bug fixes that address known vulnerabilities.
-
Download from Trusted Sources: Only download VLC from the official website or reputable sources to avoid tampered versions or malware-infected copies.
-
Exercise Caution with Media Files: Be cautious when opening media files from unknown or untrusted sources. Malicious files can exploit vulnerabilities in media players like VLC to compromise your system.
-
Use Antivirus Software: Having reliable antivirus software installed on your system can provide an additional layer of protection against malware and other security threats, including attempts to exploit vulnerabilities in VLC.
-
Report Security Issues: If you encounter any security vulnerabilities or suspicious activities related to VLC, report them to the VLC development team or relevant authorities promptly. Your actions can help protect other users and contribute to the overall security of VLC Media Player.
In conclusion, while vulnerabilities in VLC Media Player may exist, the notion of “VLC Media hacking” is often misconstrued. VLC remains a trusted and reliable media player, backed by a dedicated team committed to security and user privacy. By following best practices for secure VLC usage and staying informed about potential security threats, users can enjoy a safe and seamless media playback experience with VLC Media Player.

